Permissions for The AI Era
Never build Permissions again. Zero-latency fine-grained authorization as a service for human, machine, and agentic identities.
Never build Permissions again. Zero-latency fine-grained authorization as a service for human and machine identities
End-to-end authorization platform anyone can use
A no-code authorization platform anyone can use.
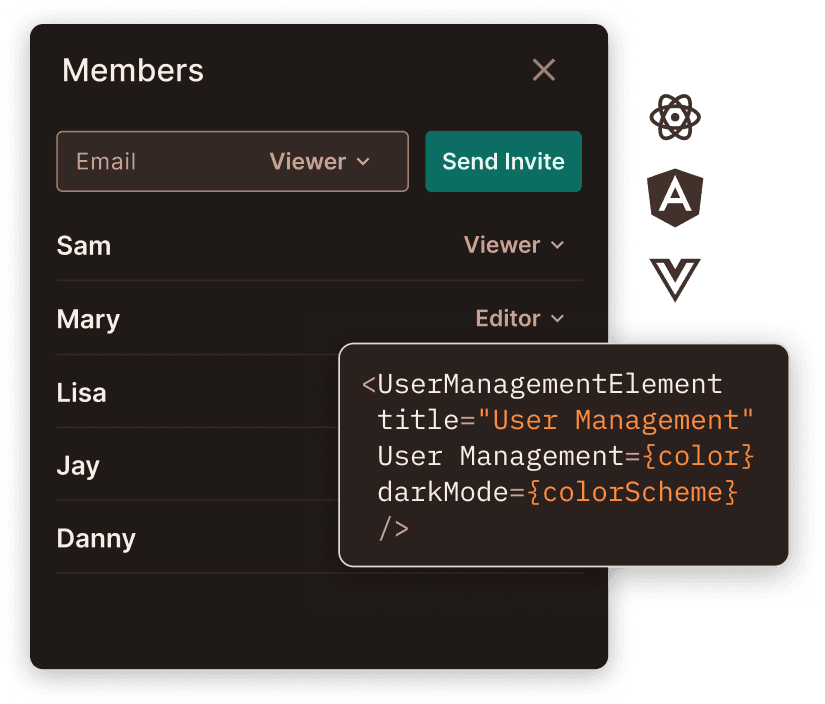
Allow your entire team - from devs to sales, to securely manage permissions
The only solution with a no-code policy editor. Supports any model - RBAC, ABAC and ReBAC.
Permit generates fully transparent policy as code based on OPA's Rego or AWS' Cedar
Everything is managed as code in Git and controlled with a simple API
Permit CLI
Developer-First Integrated Authorization
Author, Automate, Test, and Deploy Authorization Policies Directly from the Command Line
One platform, any use case
RBAC
Role based access
Create dynamic Role Based Access Control policies, like:
" Banker can Approve Loan "
ABAC
Granular attributes
Build nuanced attribute based access control policies by adding attributes, like:
" Weekend Shift Employees
can access Database during Weekend "ReBAC
Resource and user hierarchies
Create policies based on relationships between users and resources, like:
" Caregiver of a Patient
can View Patient's Medical Files "
Fully functional authorization in 5 minutes
Just add permit.check() to your code, middleware, mesh, or API gateway.
Seamlessly migrate from any existing authorization solution
GitOps and Multi-tenancy
available out-of-the-box
Hybrid Model
Secure, event-driven, compliant.
Engines
OPA / Cedar
Policy Updater
OPAL
All authorization decisions are made on your side with zero latency
Use sensitive data for authorization decisions, without it ever leaving your VPC/Network
Permit is always up (+99.99) - but you are not dependent on our availability
Compliant with HIPAA, SOC2, and more
How the Hybrid Model fits your architecture?
Flexible, Customizable, and Scalable Implementation
Supports any Authentication provider




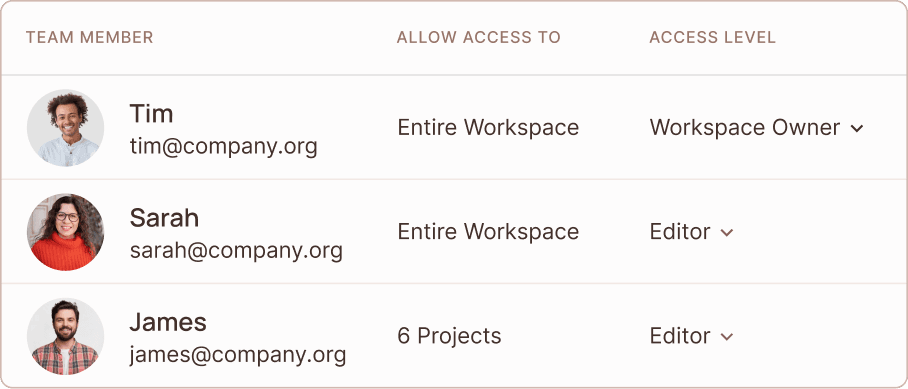
All of your access control needs in one place.
Got questions? Talk with our devs.
Works great for any industry
Tal Saiag
Granulate Founder & CTO
At Granulate we optimize our customers’ most critical systems; as a result, getting access control right is of the highest importance. Full stack permissions as a service allows our developers to focus on their core product. I was extremely impressed both by Permit.io’s technology and its dedication to customer service.
Matan Bakshi
Buzzer.ai Founder & CTO
Building authorization for Buzzer’s call-rep on-demand service was a challenging task, but with Permit.io we were able to get it up and running end-to-end in just a few days.
Ran Ribenzaft
Cisco, Epsagon CTO
At Epsagon (acquired by Cisco) we are no strangers to the complexity of microservices. Access control demands of microservices are never-ending , so they require a modern stack that can quickly adapt to the most demanding tech and security needs.
Nate Young
CIO, Maricopa County Recorder's Office
Permit’s intuitive policy editor allows access to complex attribute-based conditions that are robust enough for our developers to use, yet simple enough for our non-technical staff to configure without the need for IT assistance
Hongbo Miao
Tesla Senior Software Engineer
Moving to modern authorization for microservices is no easy feat, but OPAL made it easy. When I was learning and exploring replicator solutions for OPA myself in my free time, I found that OPAL is a very mature solution for the open-policy administration layer and beyond.
Jean Philippe Boul
Co-founder & COO Jules AI
At Jules we aim to streamline the process of buying/selling recycled materials, and sharing access as part of our portal is an important step to achieve that. Allowing users to share access is both important to get right and hard to do so, we're delighted to have Permit solve this problem for us end to end.
Test in minutes, go to prod in days.
Get Started NowJoin our Community
2938 Members