Relationship-Based Access Control with Permit
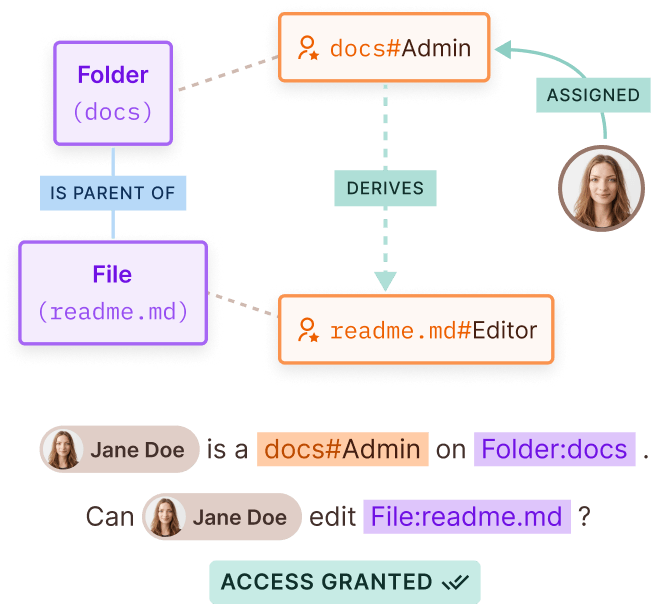
Relationship Based Access Control
Implementing ReBAC has never been easier
Manage access in your app based on relationships between users and resources with an easy-to-use, low-code interface
Start Now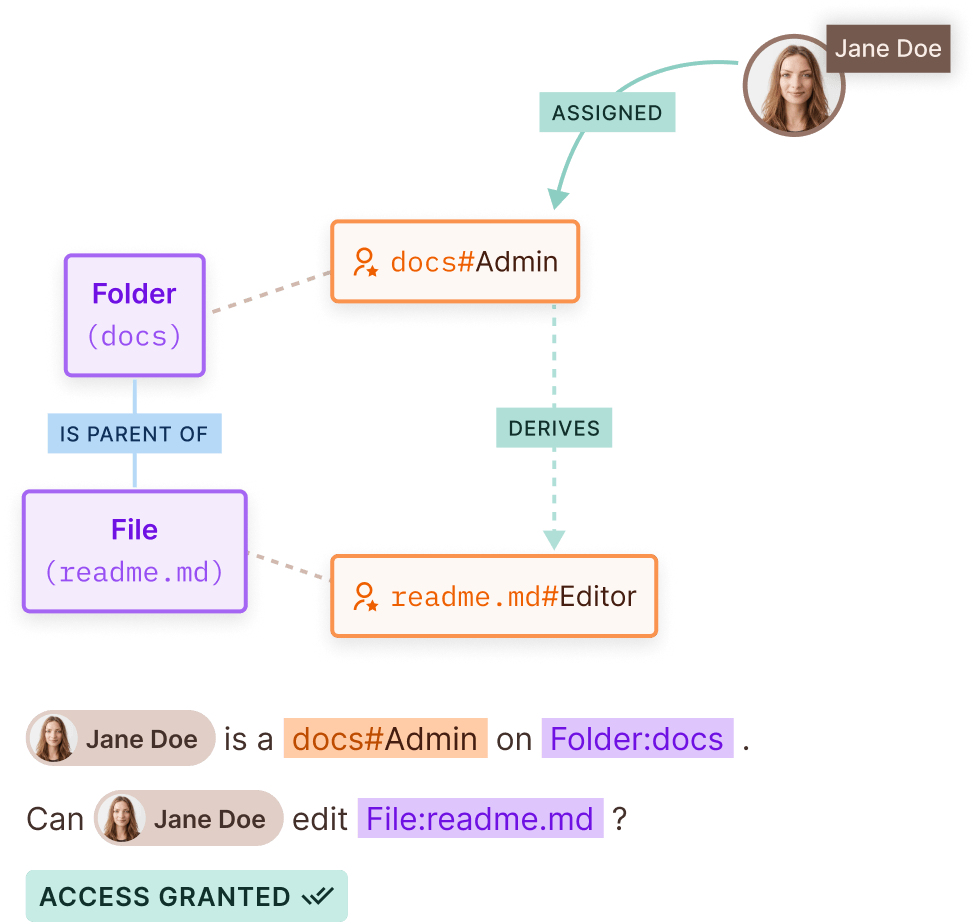
Still deciding between RBAC, ABAC, and ReBAC? Find the right authorization model for you ->Deciding between RBAC, ABAC, and
ReBAC? Learn More ->
Author ReBAC policies with ease
Effortless policy creation and management
Effortless creation and management
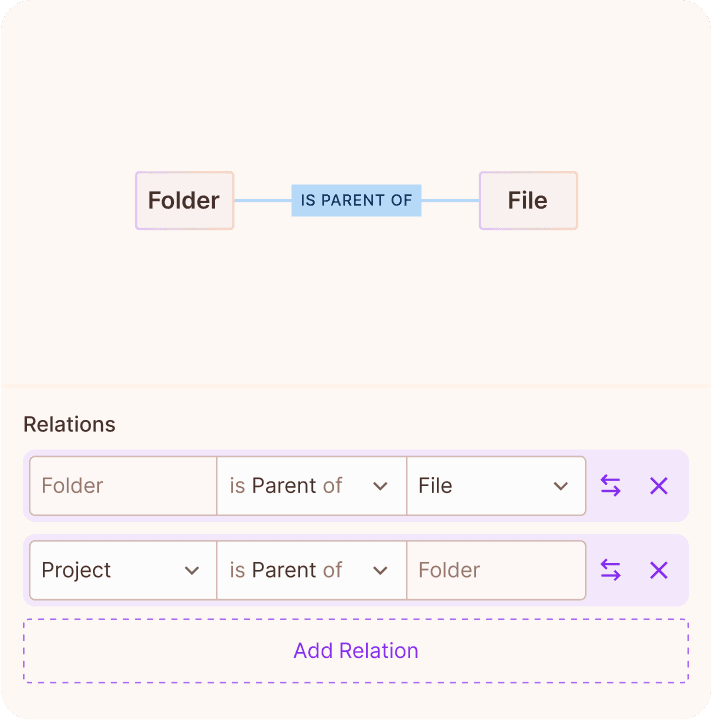
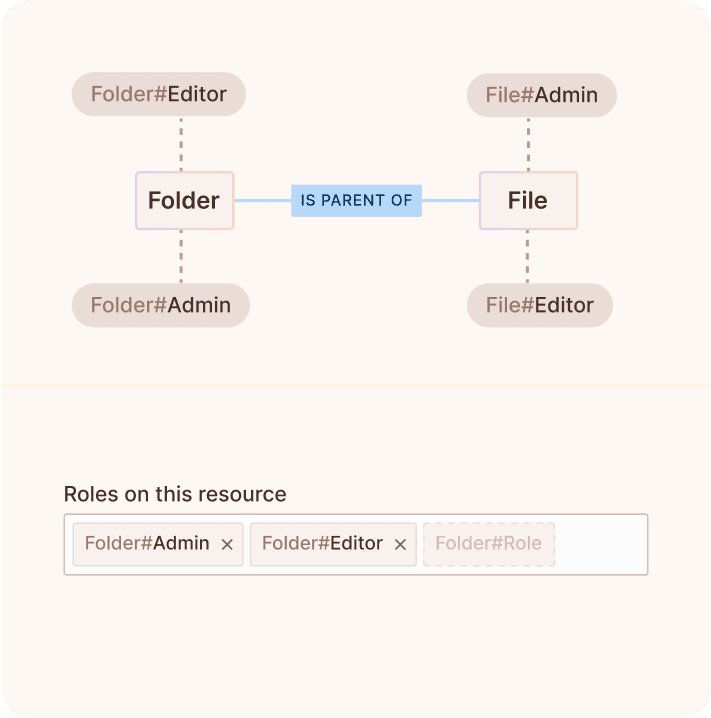
Create and manage complex Google Zanzibar style relationship graphs with the click of a button in an easy-to-use, fully customizable, no-code UI or via API.
Create and manage complex Google Zanzibar style relationship graphs with an easy-to-use, fully customizable, no-code UI or via API.
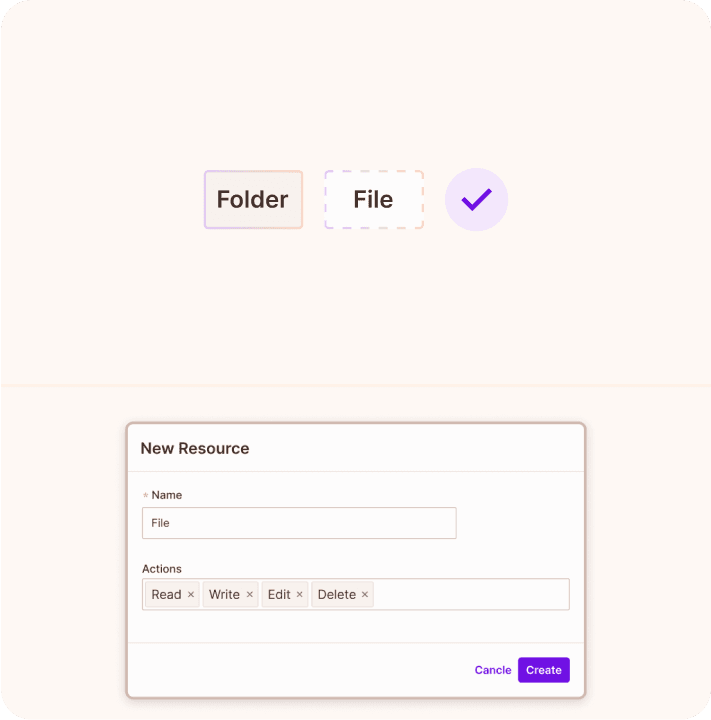
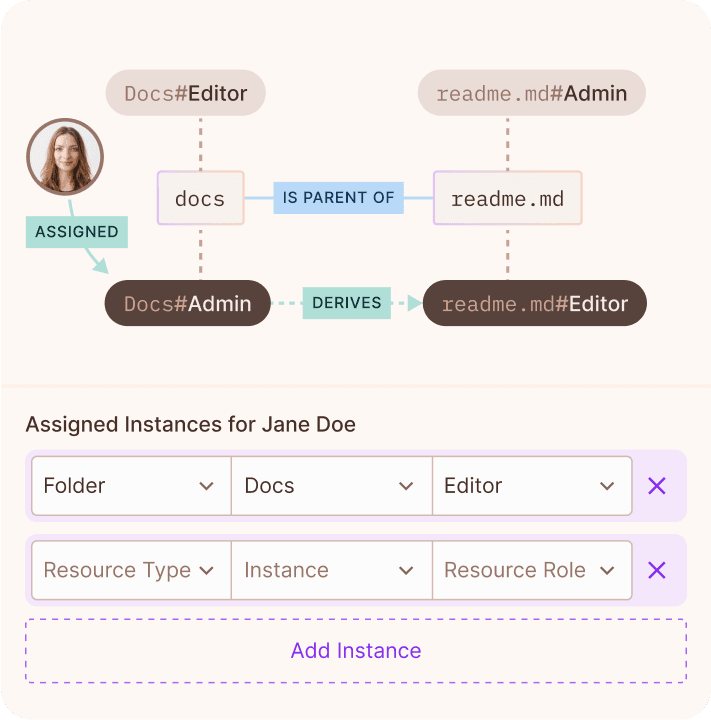
Create Resources
Define the resources you want to manage permissions for.
APIs for everything
Create, manage and automate your policies with Permit's API.
Anything done via the UI can be done with our API as well!
curl -L X POST"https://api.permit.io/v2/schema/{project_id}/{env_id}/resources"-H 'authorization: Bearer API_SECRET_KEY'--data-raw '{"key":"folder","name":"Folder","actions":{"create":{}, "edit":{},"view":{}}}'curl "https://api.permit.io/v2/schema/{project_id}/{env_id}/resources"-H 'authorization: Bearer API_SECRET_KEY'--data-raw '{"key":"file","name":"File","actions":{"create":{}, "edit":{},"view":{}}}'
Zero latency, fine granularity
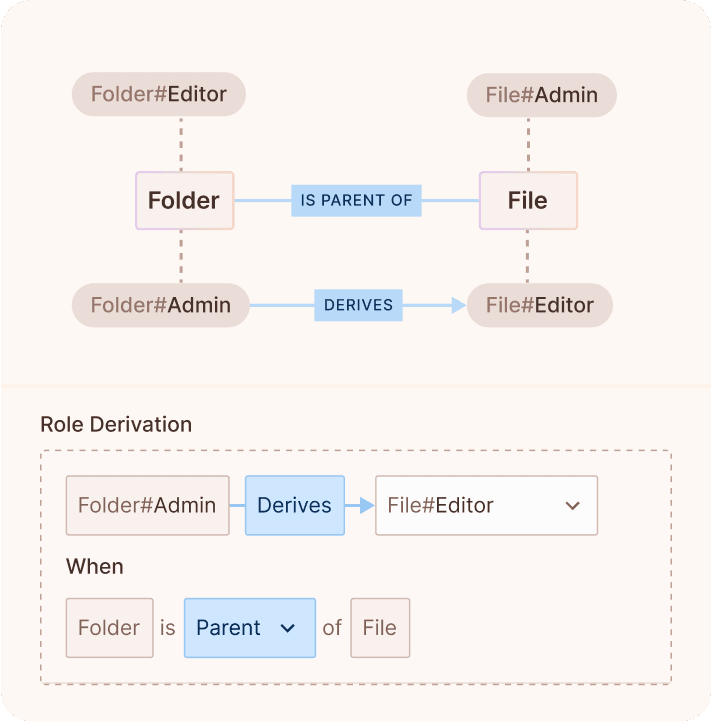
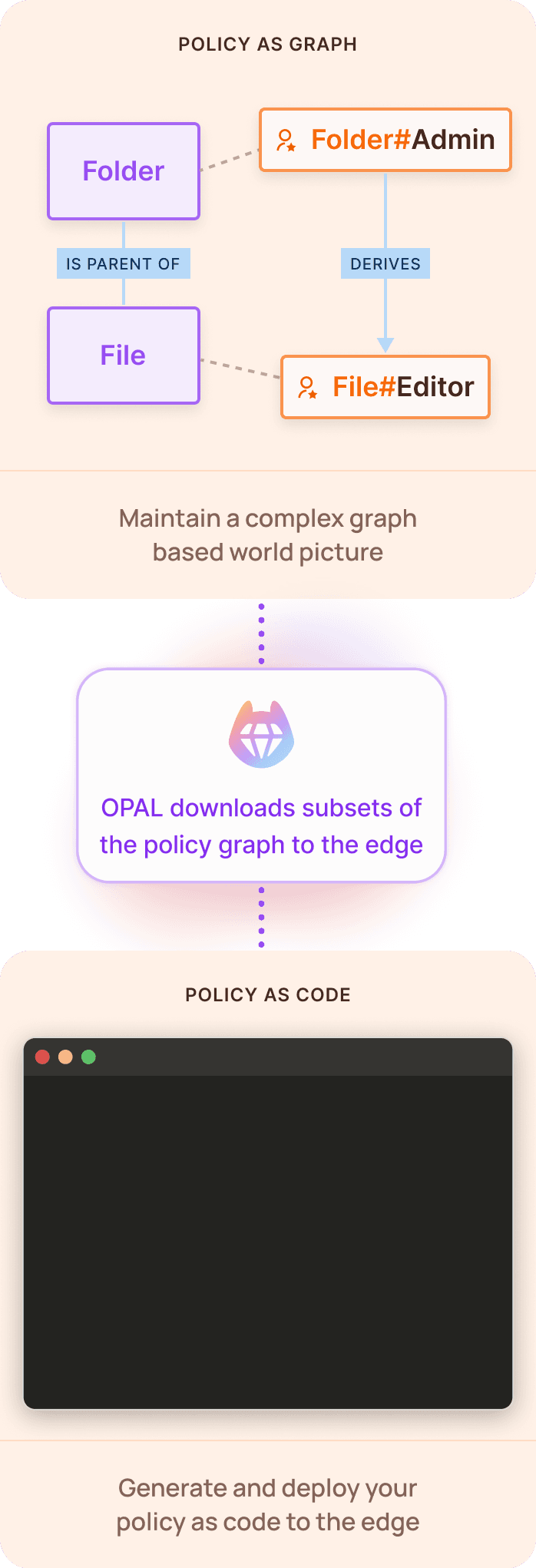
Policy as a graph? Policy as code? Enjoy both with OPAL
Combine the power of Google Zanzibar style authorization in the cloud with zero latency at the edge thanks to Permit's OPAL (Open Policy Administration Layer)
package app.rebacimport future.keywords.infiles[id] := file_instance { some file_instance in data.files id := sprintf("file:%s",[file_instance.id]) }folders[id] := folder_instance { some team_instance in data.folders id := sprintf("team:%s",[folder_instance.id]) }full_graph[subject] := ref_object { some subject, object_instance in object.union_n([files, files.folders]) ref_object := [object.get(object_instance, "parent_id", null)] }users[id] := user { some user in data.users id := user.id }input_user := users[input.user]callowing_assignments[assignment] { some assignment in input_user.assignments input.action in data.roles[assignment.role].grants assignment.resource in graph.reachable(full_graph, {input.resource}) }default allow := falseallow { count(allowing_assignments) > 0 }
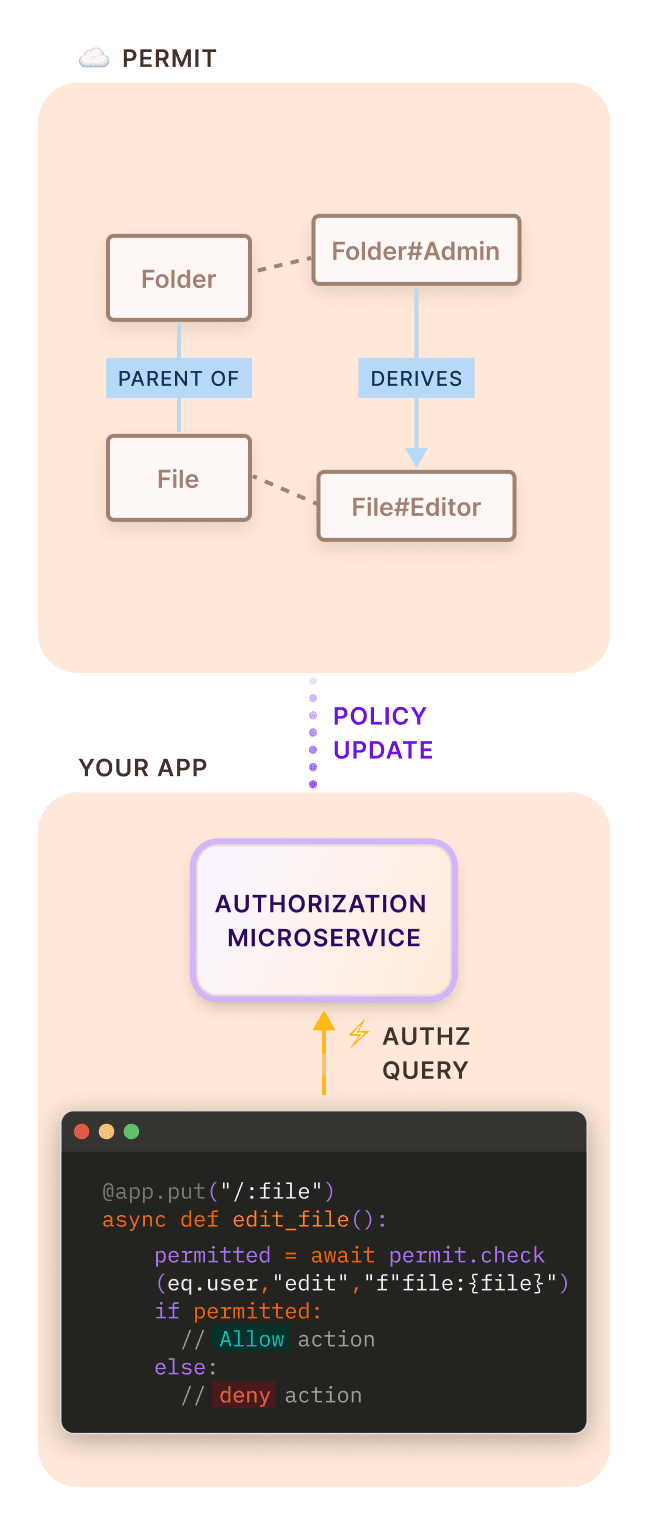
Zero latency Permission enforcement
Permit.check() in your app
Adding Permit to your app is as easy as calling a function permit.check (identity, resource, action)
Effortlessly combine and migrate between policy models (RBAC, ABAC and ReBAC) - without changing a single line of code
Quickstart DocsCan Permit handle your production scale?
Learn MoreFully flexible policy modeling
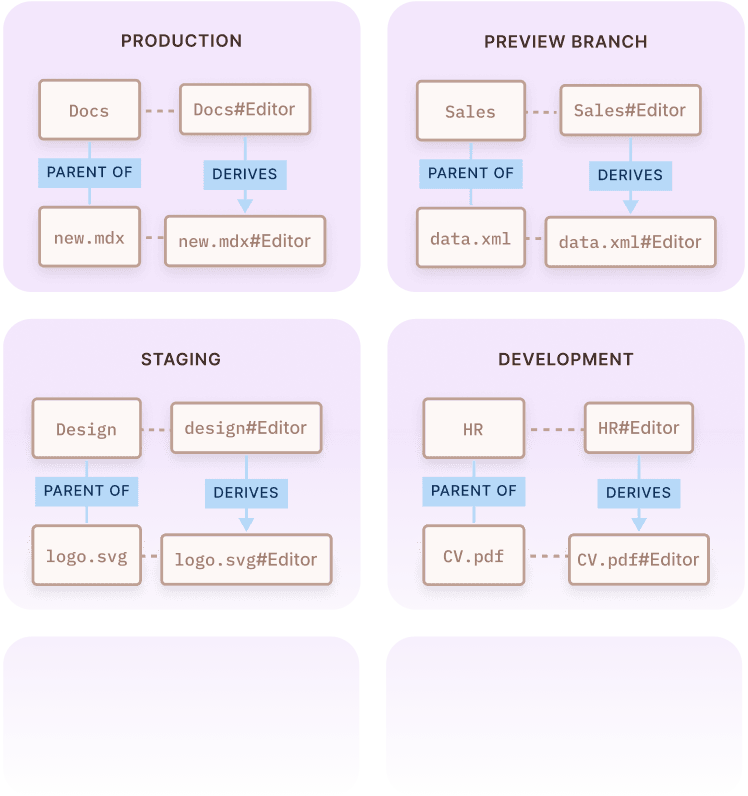
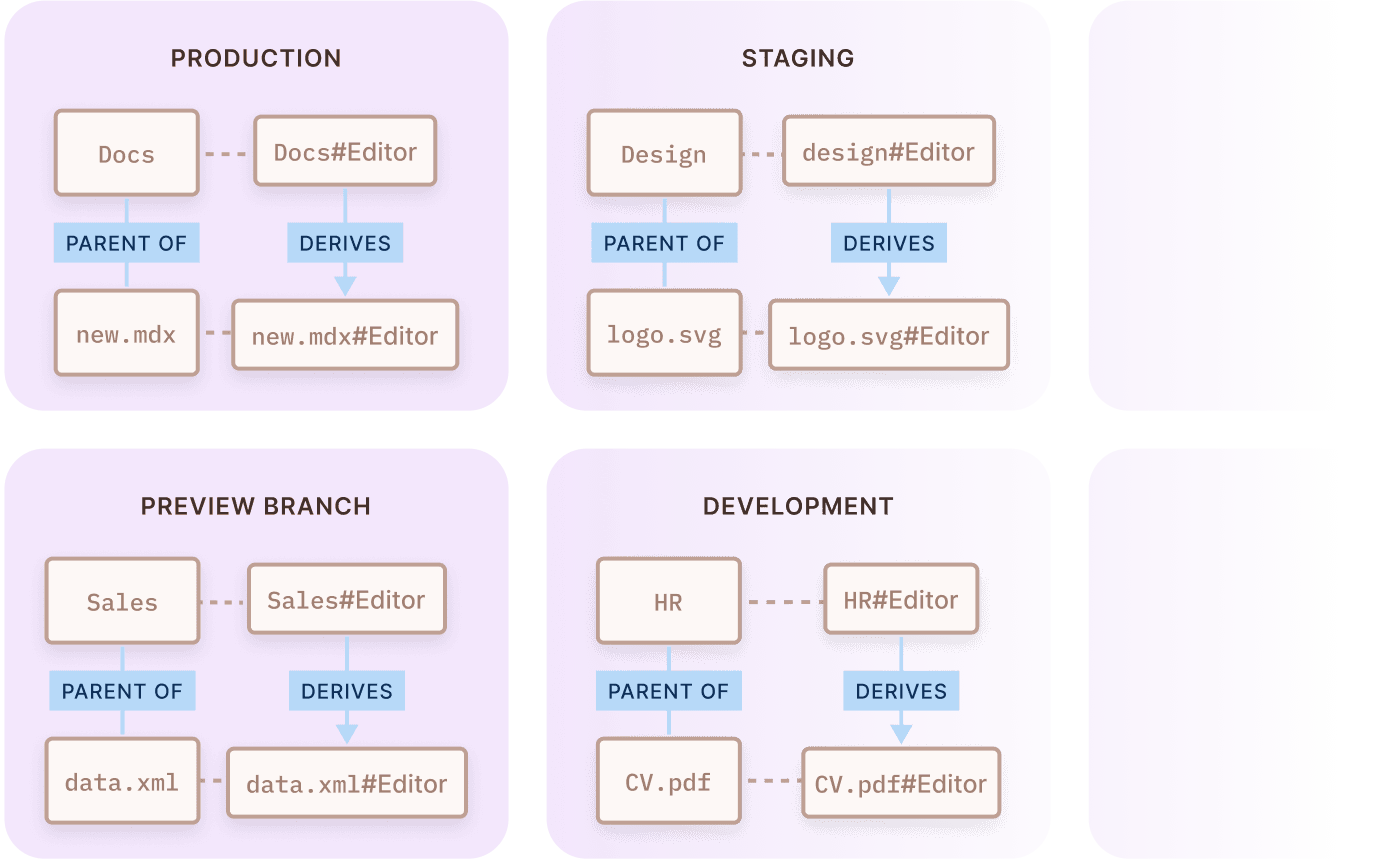
Projects, Envs
and Multi-Tenancy - All out of the box.
Model ReBAC permissions for multiple projects, environments and tenants in one unified interface.
Relationships, role assignments and derivations defined for each environment are unique, allowing complete policy separation between silos.