Best Practices for Authentication and Authorization in API

- Share:
Introduction
Strong access control is a major concern when it comes to API security - protecting against unauthorized data access and manipulation. This article delves into the various aspects of authentication and authorization in API development, specifically focusing on REST APIs.
Authentication and Authorization: Unraveling the Duo
Authentication and Authorization, though often mentioned in the same breath, serve distinct purposes in API security. Authentication validates the identity of users or systems attempting to access the API. This process establishes the 'who' in the interaction, ensuring that the entity making the request is indeed who they claim to be.
On the other hand, authorization comes into play post-authentication, determining the extent of access and actions permitted for the authenticated entity within the API. This step decides what an authenticated user or system can do, which resources they can access, and the operations they can perform.
REST APIs
REST APIs demand a fine-grained approach to authentication and authorization. As they are stateless, each request must contain all the information necessary for processing. Access control in this context must ensure seamless security without retaining user states, a challenge traditional session-based methods struggle to address.
The statelessness of REST architecture also influences the choice of authentication and authorization methods. Token-based authentication has become a frontrunner because it can carry sufficient user context in a stateless manner. Similarly, authorization techniques must be decoupled from the API logic to have a light footprint in the API code yet be powerful enough to handle complex access control requirements inherent in RESTful services.
Navigating the Spectrum of Auth Personas:
Various personas emerge in API authentication, each with unique authentication needs. Let's go over them:
- End Users: Often the primary persona, they interact with APIs indirectly through client applications. For them, methods like OAuth 2.0 provide seamless access without compromising security. As an example for an end user, imagine a mobile app leveraging OAuth 2.0 for logging in via social media accounts.
- Applications: These non-human entities require distinct authentication approaches. The basic usage of such an application is service-to-service communication without access to specific client data (think of observability services), but it could also require authorization on behalf of the user permissions. For this scenario, Client credentials flow, a subset of OAuth 2.0, is typically used where applications authenticate using their own identities rather than representing a user.
- Ingress Entities: The internal service-to-service communication in microservices and distributed applications has its own auth requirements. Due to the nature of ingress calls, they need less inspection into tokens as the data is encapsulated, yet the permissions and data management should be fine-grained and allow access only to the relevant data.
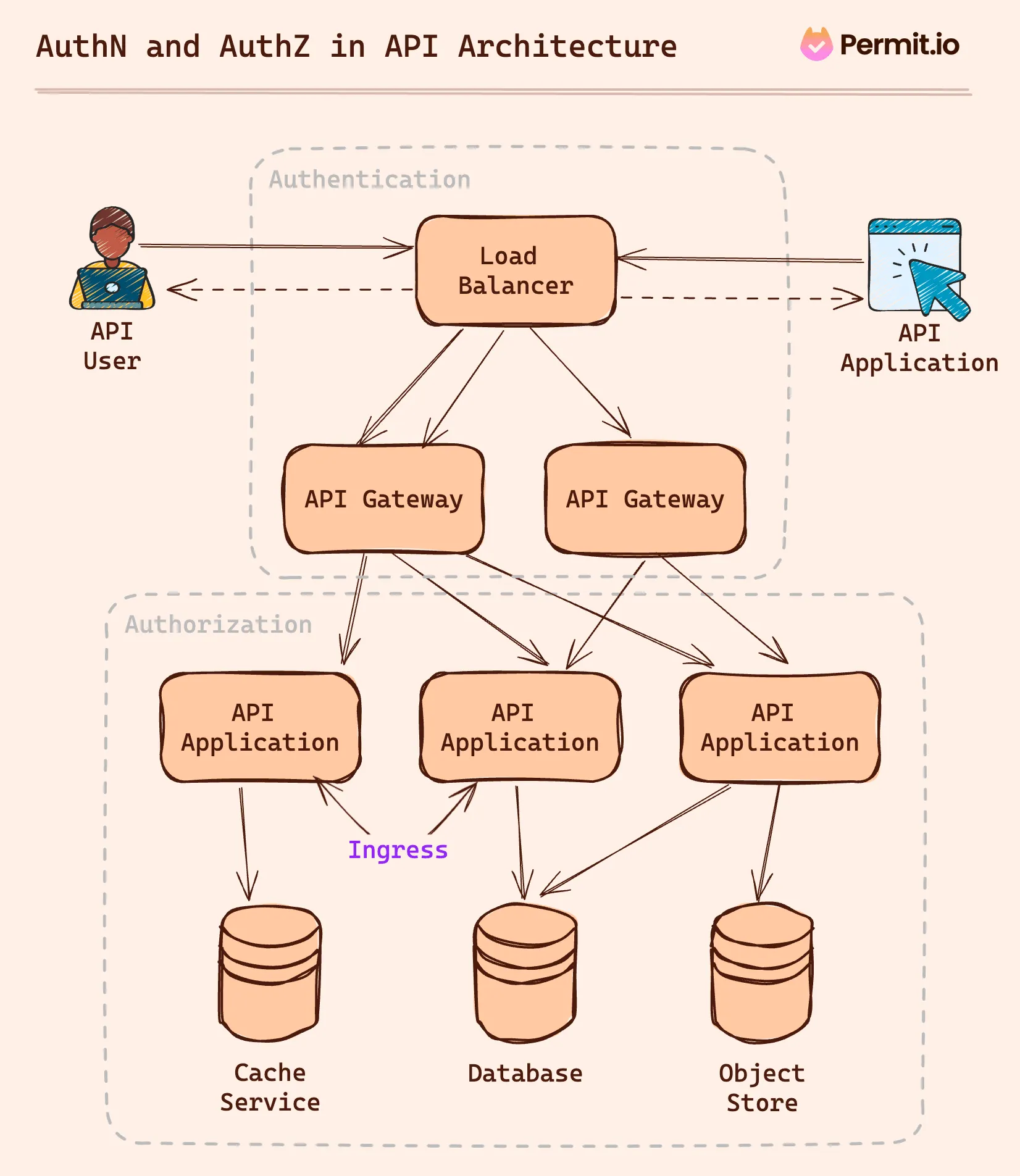
Auth Stages: The Journey of an API Call
API calls go through various stages, each with its own security implications. Let's map out these stages:
- Load Balancer: Being the initial touchpoint, it distributes incoming API calls. With a primary focus on traffic management, it can also perform initial authentication checks, like validating API keys.
- API Gateway: A critical security checkpoint, it often handles detailed authentication and authorization. Gateways can enforce policies, validate tokens, and ensure only authenticated requests can proceed.
- Application Code: Here, more granular authorization checks occur. The code determines if the authenticated entity has the necessary permissions for the requested operation.
- Data Layer: The final layer where data access and manipulation happen. Even at this stage, checks are essential to ensure compliance with the principle of least privilege.
Authentication and Authorization Across Stages
In the load balancer and API gateway stages, authentication predominantly involves verifying the requester's identity, often through API keys or tokens. The focus here is to ascertain if the caller is who they claim to be. Basic authorization can happen at this point using policy engines connected to the API gateway.
Once in the application code, the scope shifts more toward authorization. It's about validating permissions: can this user or service perform the requested action? This is where roles and policies come into play, delineating the boundaries of what each authenticated entity is allowed to do.
Finally, at the data layer, data filtering and partial evaluation authorization checks ensure data security and integrity, restricting data access to only those entities with appropriate rights.
Token-Based Authentication: The New Norm
Session-based authentication methods are becoming relics of the past in the world of APIs. Their reliance on server-side state management just doesn’t fit with the stateless nature of REST APIs. Each API call in a session-based approach requires server-side context, a difficult requirement to handle in scalable, distributed environments.
Token-based authentication, on the other hand, especially JSON Web Tokens (JWT), has become the gold standard in API authentication. JWTs encapsulate user identity and claims in a compact, self-contained format, making them ideal for stateless RESTful environments.
Think of an end-user accessing a web application. The application might use an OAuth 2.0 flow, where an external identity provider authenticates the user, and a token is issued. This token is then used for subsequent API calls, neatly encapsulating the user's identity and permissions.
For service-to-service (application-to-application) interactions, JWT tokens are exchanged, where each service authenticates the other using tokens signed with secure keys. This method ensures that each service is verifiable and trusted within the architecture.
Policy as Code for Authorization
Policy as Code represents a significant shift in managing and enforcing authorization rules. It involves defining security and operational policies in code, making them more dynamic, scalable, and maintainable. This approach aligns perfectly with modern infrastructure-as-code practices.
In the context of APIs, Policy as Code allows for flexible, context-aware authorization that can adapt to complex and changing requirements. It supports a decentralized approach, where policies are defined alongside the resources they protect, enhancing visibility and control.
OPAL (Open Policy Administration Layer) is an open-source project that facilitates policy-based authorization in APIs. It provides a real-time policy engine that integrates seamlessly with API infrastructures, allowing developers to easily enforce granular, context-driven policies. Here’s an example of using OPAL in a FastAPI application to enforce fine-grained authorization.
Authentication Best Practices
Essential Practices for Robust API Authentication
- Use Strong Authentication Mechanisms: Prefer token-based mechanisms like OAuth 2.0 and JWT for their robustness and suitability for RESTful APIs.
- Implement Rate Limiting and Throttling: Protect APIs against brute-force attacks by limiting the number of authentication attempts.
- Employ Multi-Factor Authentication (MFA): Add an extra layer of security beyond just passwords or tokens for critical applications.
- Regularly Rotate and Refresh Tokens: Prevent token misuse by setting expiration and enabling automatic token refresh mechanisms.
- Secure Token Storage and Transmission: Always use HTTPS for API calls and securely store tokens to prevent leakage.
- Monitor and Log Authentication Attempts: Keep a close eye on authentication patterns to detect and respond to suspicious activities.
Authorization Best Practices
Key Strategies for Effective API Authorization
- Decouple policy from application code: Tools like OPAL enable dynamic and context-aware policy enforcement, making authorization more adaptive and scalable.
- Employ the Principle of Least Privilege: Grant users and services the minimum permissions necessary to perform their functions. This reduces the risk surface in case of compromised credentials.
- Start with Role-Based Access Control (RBAC): Define roles and associate them with specific access rights. This simplifies managing permissions, especially in large-scale systems.
- Scale to Fine-Grained Access Control: Implement detailed policies that control access at the level of individual resources or operations.
- Regular Policy Reviews and Updates: Continuously evaluate and update access policies to reflect changing requirements and threat landscapes.
- Audit and Monitor Authorization Decisions: Keep detailed logs of authorization decisions to track access patterns and detect potential breaches or misuse.
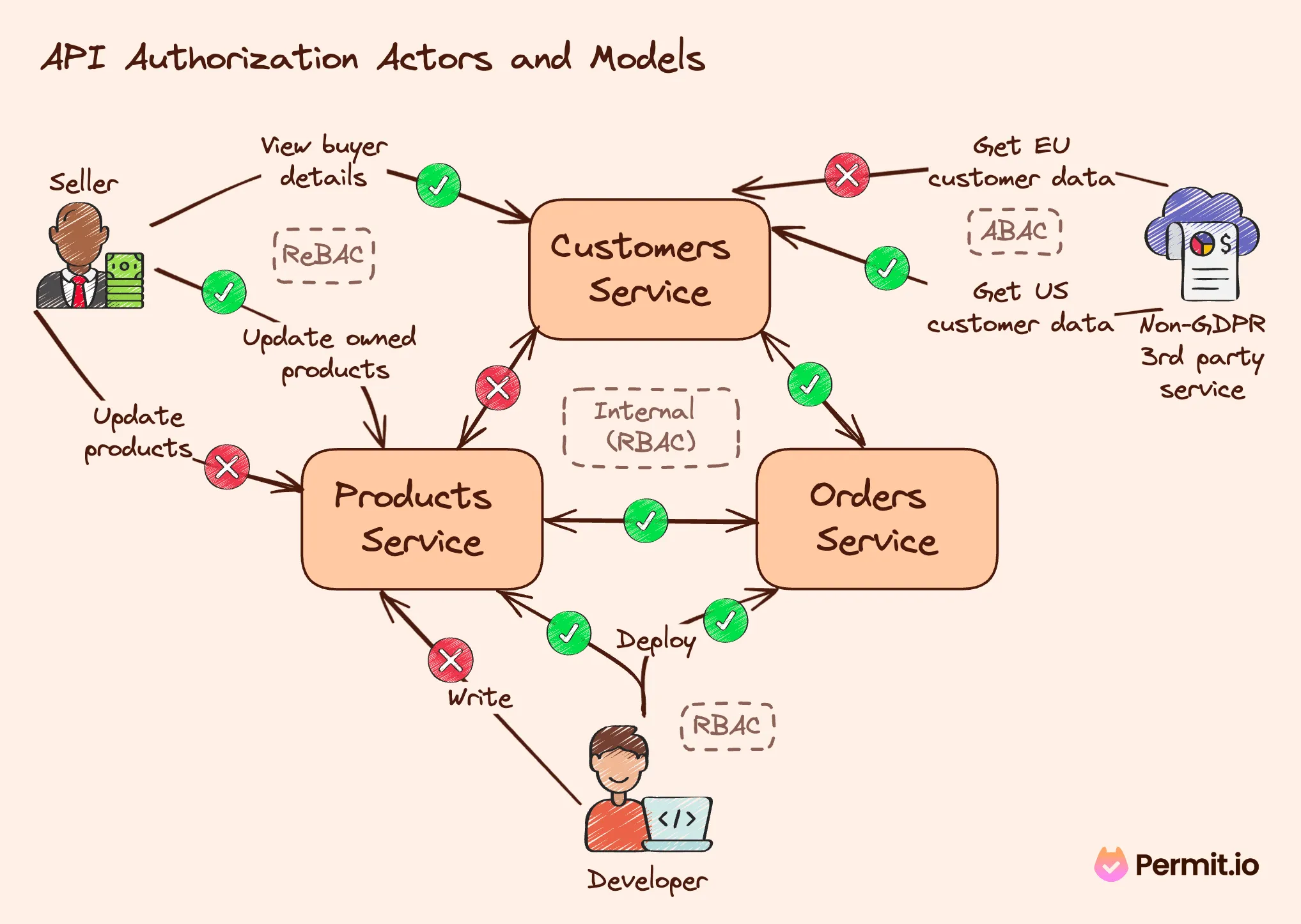
The following diagram illustrates how common permission models are incorporated in API applications. You can learn more about designing and implementing better authorization in APIs here.
Testing Auth in APIs
Thorough testing is critical in the authentication and authorization landscape of APIs. This ensures that security mechanisms work as intended and can withstand various attack vectors.
Maintaining different testing environments, such as staging and production, allows for thorough testing without compromising real-world data or operations. Automated testing frameworks can simulate various authentication and authorization scenarios, providing comprehensive coverage.
Token-based authentication and Policy as Code methodologies are well suited to automated testing, with tokens being programmatically generated to test different authentication scenarios. Similarly, Policy as Code allows for automated testing of various authorization policies, ensuring they enforce the intended access controls.
What Next?
Analyzing gaps in current practices is essential for continual improvement. Tools and practices should be periodically reviewed and aligned with emerging best practices and threats.
We encourage you to take part and contribute to open-source projects like OPAL, and leverage their capabilities in their API security strategies. Want to support the project? Star OPAL on GitHub, explore its functionalities, and integrate it into your API security framework.
Written by

Gabriel L. Manor
Full-Stack Software Technical Leader | Security, JavaScript, DevRel, OPA | Writer and Public Speaker


